What does Tallahassee, Stuart, Riviera, Lake City and Sarasota and newly added to the list Key Biscayne have in common? Spectacular Golfing? How about victims of cyberattacks?
The news has been full of information over the past week because another Florida city, this time Key Biscayne (right after Lake City) was the victim of a ransomware email attack.
How does this work? Let’s say you work for the city of Metropolis, Florida and you are in the HR department.
Say your name is Bruce. You receive an email with a subject line, “Hi, Bruce.” The email appears to be coming from Monster.com; it says your resumes from a job search are attached.
At first, you think, “didn’t we stop using Monster?” You also may have assumed it was someone else’s job to review resumes this year. Nevertheless, you don’t want to miss anything.
So, you click. TOAST.
The infection embedded in the link spreads instantly.
Now, Metropolis is hosed. Any city services (and users on the same network) are infected also.
Potentially, it could affect everything from the police department to trash pickup, depending on how the city’s network is set up.
How did this happen?
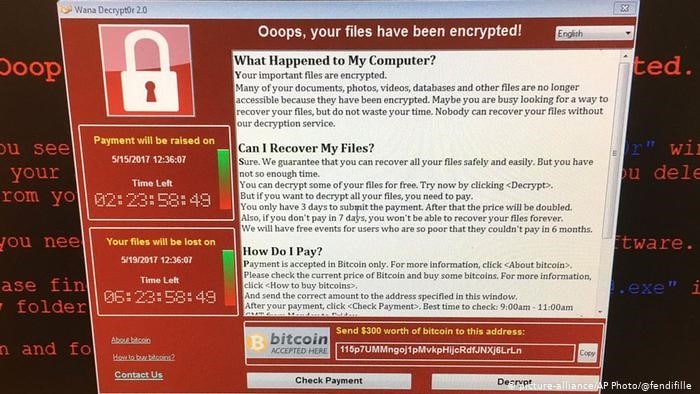
Hackers found Bruce on the internet, put together an email that appears legit to his job — getting him to click. Now there are two choices: either 1) restore your network from a backup or 2) send the hackers the ransom and they give you decryption keys to unlock the attack — or they don’t (in some cases; they are criminals, after all).
Here is a sample screenshot of a common ransomware attack once you click …
So, by now you should know that part of the story.
But the most interesting (and frightening) part is what people are not talking about regarding the evolution of this type of attack.
It’s the dollars.
From a few thousand from a small business a couple of years ago, to (let’s say) $25,000 from a hospital last year to half a million today. This is where the story is. And this is unwelcome news for anyone in city government.
Now hackers are realizing that cities have deep pockets, and why ask for a couple of thousand dollars when you can demand several hundred thousand?
So, what’s next? Every hacker around the globe is seeing how vulnerable these areas are; they are targeting them more and more.
Using more innovative templates and more devious socially engineered attacks. How much are people willing to pay? There was a $935,000 ransom paid last year.
These criminals are still testing the waters for what they can get away with. They are going straight up Austin Powers on us. We would like … ummm … 1 MILLION DOLLARS, please.
If the city of Baltimore paid $18 million to get back up and running, the ceiling for this type of thing has not yet been reached. Expect the next one to ask for a million plus.
(For the record, Baltimore refused to pay the ransom)
How bad is it? Check out the FBI’s cybercrime page, under key priorities — ransomware is No. 2.
This is further complicated for everyone by the fact that it is almost impossible to catch these criminals because they are using untraceable tools and currency.
This kind of attack will happen increasingly until people stop falling for it, or the criminals get caught.
Unfortunately, neither of those scenarios are likely to happen any time soon.
___
Blake Dowling is CEO of Aegis Business Technologies. He can be reached at [email protected].