 Ransomware has become the fastest growing cyber threat; last week it was a variation called Fatboy, this week is WannaCry. The criminals are targeting everyone from home users to health care systems to big business. Data show that there has been an average of more than 4,000 ransomware attacks every day of this year. That is some serious volume.
Ransomware has become the fastest growing cyber threat; last week it was a variation called Fatboy, this week is WannaCry. The criminals are targeting everyone from home users to health care systems to big business. Data show that there has been an average of more than 4,000 ransomware attacks every day of this year. That is some serious volume.
I know of a dozen entities that have been hit, some hit hard, like 1997 John Lynch chasing you down.
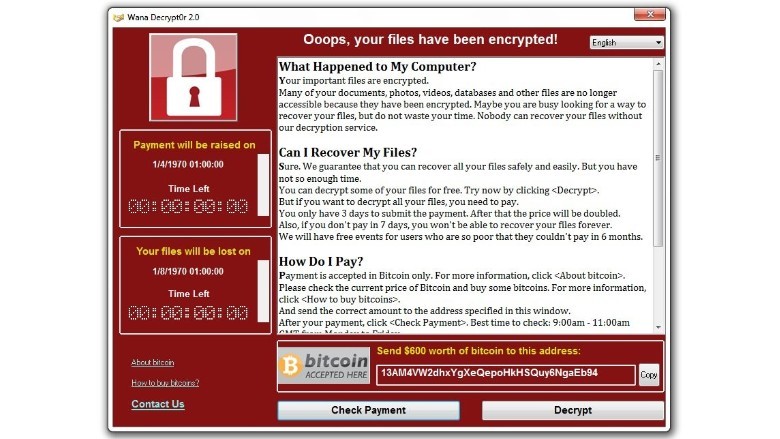
On May 12, information technology professionals began tracking a new ransomware variant that spread rapidly throughout the weekend. It is a highly virulent strain of a self-replicating ransomware that has affected organizations like the Russian Interior Ministry, Chinese Universities, Hungarian and Spanish Telcos, as well hospitals and clinics run by the British National Health Services.
It is especially notable for its multi-language ransom demands that support every major language on the planet. These criminals need to be hunted down now.
Patients’ lives were put on the line in Britain. Surgeries and procedures were delayed. I have not heard of any fatalities, but the hammer of justice needs to find these cyber-weasels STAT.

On to the techy details, this ransomware is being called several names: WannaCry, WanaCrypt0r, WannaCrypt or Wana Decrypt0r. It is spread through an alleged National Security Agency exploit (I said “alleged” NSA, don’t come looking for me) called ETERNALBLUE that was exposed online in March by the hacking syndicate Shadow Brokers.
ETERNALBLUE exploits a vulnerability in the Microsoft Server Message Block 1.0 (SMBv1) protocol.
Bottom line: make sure someone manages your technology.
Make sure someone has been reviewing, confirming, patching, and applying any current updates that may put added security to your firewall, operating systems (if you are still running Windows XP, you fail), anti-virus and anti-spam solutions.
It is most important that now and going forward that you and your users do not click on emails that hold the following threats; (some may get through these layers of security).
Emails from HR Professionals claiming to include resumes, financial institutions, and shipping companies are some of the most common.
Be extremely wary of any Microsoft Office email attachment that recommends you enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros. Instead, delete the email at once.
This latest attack stayed on the other side of the pond – for now – but thanks to technology, our world is inner-connected like never before.
We will see something new and more devious before you can say “Putnam for Governor.”
___
Blake Dowling is CEO of Aegis Business Technologies and can be reached at [email protected].